End-to-End Trust and Security in the IoT
Day one of the IEEE IoT security events delivered everything it promised and more. The speakers were well-informed and provocative, and the breakout sessions produced some actionable ideas as well as some that will cause some observers of the IoT space to question their assumptions.
Four breakout sessions examined the state of technology in key areas: 1) Access control and authentication; 2) System architectures for security; 3) Standards and policy; and 4) Scenarios and Use Cases. Reports of these sessions highlighted the wide scope and variability of security technologies, but the fundamental message is the need to take a holistic, system-centric view of the trust and security problem.
The whole system view was especially evident in the architecture breakout session I attended. A paper on ontology-based analysis was especially helpful. When engineers use the term “ontology” it means a view of systems that includes both a traditional taxonomy of elements of the system as well as an inventory of the messages that pass between components and the range of interactions between systems elements. So it’s not like the ontology of the philosophers.
One speaker declared security a “solved problem” for smart grid systems based on a novel method that examines the grid as a whole and looks for deviations from normal operational parameters. This approach comes out of the National Renewable Energy Lab, which happens to be located close to my home in Colorado, so I’ll be checking it out.
The access control and authentication group also concluded that the “solved problem” tag applies to the component parts of their problem space, if not to the actual usage. That is simply to say that shared secrets, passwords or biometric, are essentially adequate for establishing user identities and don’t even need to be supplemented by two-factor authentication for the most part.
But that’s not to say the people use strong passwords or that systems are designed in such a way that people are encouraged to use strong passwords. This is an area that needs a lot of work by operating systems and application designers.
Strong, unique passwords across the Internet space require the use of a password manager, and some players (Visa, for example) have designed their systems in such a way as to make use of password managers as difficult as possible; you can’t copy-paste a password into Visa’s web system, you have to type it. Visas insists they’re experts in this field, but forcing people to type passwords from a smart phone means the passwords we choose will be easy to type but not very hard to guess.
The missing link in this space is the combination of security tools with good human factors design. Apple, for example, requires user passwords to be re-entered several times to form some particular maintenance and update tasks. This should never happen.
The Day Two event is getting started, so updates to follow as things roll along.
UPDATES: We begin the with introductions; it’s good to see a number of distinguished academics and members of DHS, the Defense Department, and the Transportation Department. Hill and regulatory staff gave this event a pass, but may be watching the webcast.
First keynote is from Juan Carlos Zuniga of InterDigital Labs, a firm that develops IP around wireless systems. Juan has been a co-chair and chair of privacy initiatives in IEEE and IETF.aYesterday he gave a presentation about dynamic vs. static identifiers in Wi-Fi that made a strong case for replacing traditional static addresses with temporary and dynamic ones.
They keynote covers privacy issues in IoT, naturally. He urges technologists to stress the technology aspects and leave the lawmaking to lawmakers. His particular technology emphasis is on the vulnerability that comes about from persistent identifiers such as network addresses and user names.
The connection between secrets and persistent identifiers caused the initial form of Wi-Fi encryption, WEP, to collapse. Because each Wi-Fi frame begins with the same pattern of bits, hackers can try random combinations until they see that pattern. So that’s a very real issue.
From the floor, William Whyte asks if it’s practical for engineers to take a purely technical approach, detached from policy, and Juan replies by pointing to the differences in international laws WRT privacy.
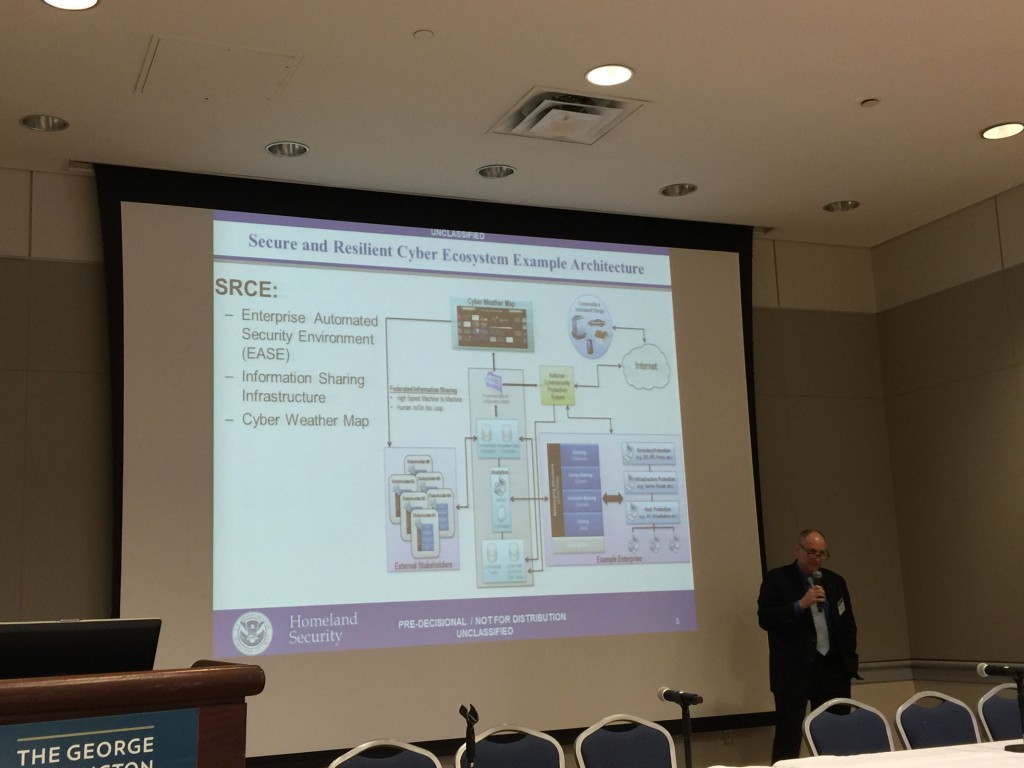
Next up, Tom Ruoff of Homeland Security gives the policy-oriented keynote. He stresses that DHS’s concept of success isn’t the same as that of ordinary people. He cares about interconnectivity of first responders and about keeping up with the sophisticated new attacks. DHS’s staffers aren’t necessarily as clever as the attackers, but DHS has information that the attackers don’t have. So making better use of the data is a key imperative.
His most intriguing observation is that we lack a resilient network with the ability to communicate securely. Interoperability, automation, trust, information sharing, and assured communications are his main bullets.
The key to Assured Communications, in DHS’s view, is
- Resilient Communications
- Priority Services
- Interconnected Infrastructures.
That’s right, Priority Services is a key element, and the main emphasis is on a secure and interoperable messaging bus, a means for the good guys to communicate with each other without the bad guys knowing what they’re saying.
I will cover the panels in a separate post.