Two Security Headaches Usher in the New Year (Updated!)
Happy New Year, here are two more things to worry about: researchers at the Princeton Center for Information Technology Policy have discovered that dodgy code in web pages can read your saved logins and passwords and use them for their own purposes.
There’s also an unrelated finding that memory security is flawed in Intel CPUs in such a way that rogue programs can read and modify operating system data.
Here’s a rundown on these two security issues and what they mean to you.
Princeton Finds Login Manager Security Issue
The Princeton exploit is probably less serious than it sounds. The researchers have been unable to find instances where user names and passwords were used for identity theft. Their concern is that possession of a user name makes tracking easier:
The underlying vulnerability of login managers to credential theft has been known for years. Much of the past discussion has focused on password exfiltration by malicious scripts through cross-site scripting (XSS) attacks. Fortunately, we haven’t found password theft on the 50,000 sites that we analyzed. Instead, we found tracking scripts embedded by the first party abusing the same technique to extract emails addresses for building tracking identifiers.
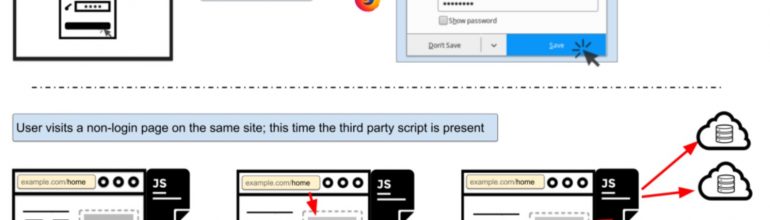
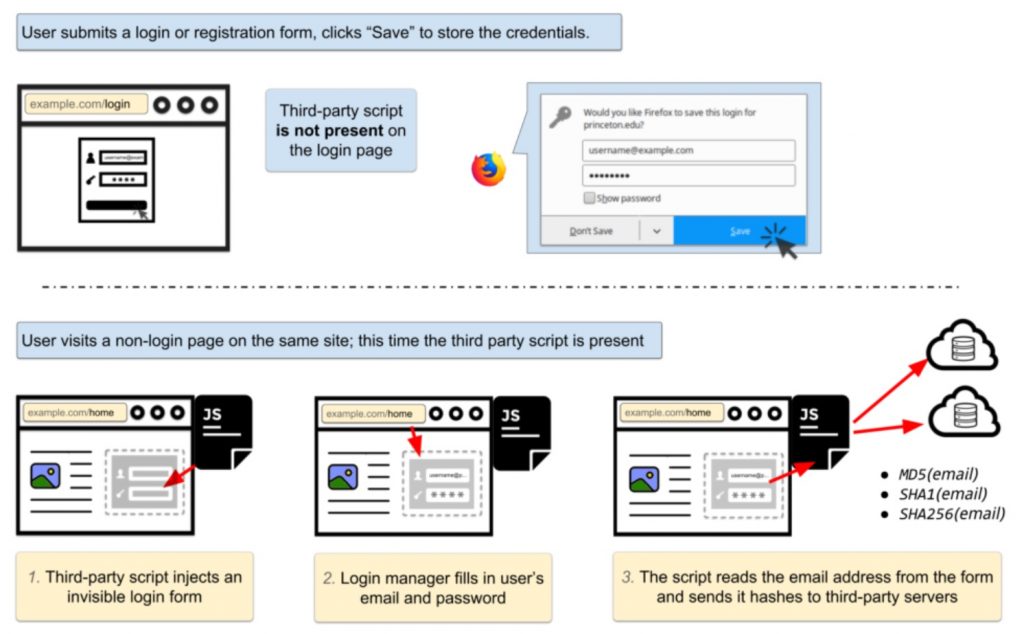
This is bad, but not not nearly as serious as it might be. In order to get the stored user name and password from the browser’s password manager, the web page needs to embed code. CITP has found the form the password manager fills in can be invisible to the user, so the credentials can be passed multiple times.
How it Works: Invisible Login Form
Here’s Princeton’s diagram. It shows an invisible web form grabbing credentials and sending them in encrypted form to a tracking database.
Security Solutions
There are two issues: 1) Some pages embed third party tracking code that takes user names and passwords; and 2) Browsers don’t seem to care whether password forms are invisible to the user. Password managers – like LastPass, 1Password, and Keeper – are somewhat more robust than built-in password managers in browsers, but they’re not 100% secure either.
You’re immunized from the problem if you use a third party password manager and don’t enable auto-fill. This prevents the password manager from sharing your credentials unless you click a form, and you won’t be able to do that to invisible forms. Keeper doesn’t support auto-fill, so you don’t need to worry about it, but most PMs enable it on a site-by-site basis.
Browsers can add code that refuses to fill invisible forms, but they haven’t done that yet. So the only other solution for people who don’t want to share user names with trackers is not to visit pages that embed third party tracking code. You’ll need a tracking detector such as Privacy Badger or Ghostery to find them. I recommend Ghostery.
Don’t let your browser save your login credentials if you don’t want to be tracked. And don’t kid yourself that you’re not going to be tracked by some other means, because you probably will be. This isn’t an ID theft exploit, it’s a way of harvesting preferences for ad targeting and resale.
Intel Memory Protection Bug Compromises Security
The Intel bug is more insidious; so much so that the security community isn’t sharing all the details until operating system patches are available. The general issue is that there are holes in Intel’s memory protection.
Modern computers support multi-tasking, obviously. Robust multi-tasking systems build walls around application programs to prevent them from modifying each other’s data or changing operating system data directly.
Typically, the operating system is hidden from the apps, but the apps are not hidden from the OS. These walls are accomplished through “virtual memory” structures that actually hide physical memory from apps. Apps see logical addresses, but the CPU translates them into physical addresses.
How it Works: Over-Eager Predictions
CPUs provide protection, but their main job is providing performance. One of the tricks to performance is called “branch prediction”, a method of preparing the CPU for the decisions programs make about how to execute code. Code does things like this all the time:
if (condition == TRUE) then a = a + 1; else a = a + 2;
When the CPU is chugging along, it has processes commands from a pipeline that enables it to do one thing after another really fast. When there’s a fork in the road, it needs to prepare for both paths. So this piece of code will cause the CPU to load both “a = a + 1” and “a = a + 2” in its branch prediction pipelines. When it knows whether the condition is true, it knows which pipeline to activate and which to discard.
It appears that Intel has been getting a little bit ahead of itself (for about ten years) by beginning to execute the instructions before fully checking the permission of the program to see the data it accesses after the branch.
If the app doesn’t have permission to access the memory location named “a”, the CPU is supposed to stop the program before it can read or write it; but that doesn’t appear to be happening.
Security Solutions
Because this is a problem of over-eager CPU acceleration, you might guess that the solution is to slow things down. That would be correct. The Linux patch apparently slows down program execution by as much as 30 percent by un-caching some program information (a virtual memory structure known as the “translation lookaside buffer”) that is currently cached:
Linus is accepting a change to the Linux kernel that flushes the TLB on system calls. This is an extraordinary performance degradation in order to fix this (as yet unknown) security bug. https://t.co/VadkwkzWQD
— Robert Graham, HODL HODL (@ErrataRob) January 2, 2018
On the most modern Intel CPUs, there’s a somewhat less drastic solution that only has a 5 percent performance hit, so lucky you if you have a new CPU. If you have an AMD CPU you’re in the clear because this is an Intel-only bug. But your AMD CPU is already slow compared to its Intel counterpart, so there’s that.
All in all, this is a bummer of a bug that makes Apple’s slowdown of older iPhones look mild by comparison. The only consolation is that you won’t feel the full impact on the web because you’re waiting for ad auctions rather than for CPU operations or network downloads anyhow.
Conclusions
Computers are complicated. One major source of complexity is components that don’t progress at the same rate. The classic example of this phenomenon is CPUs – which are bred for speed – and dynamic RAM, bred for density. Because CPUs are faster than DRAM, they’re full of caches and pipelines to boost the availability of data from memory to CPUs.
Complex systems are hard to build and even harder to test and verify. So bugs like this one can slip through the cracks for decades without being fixed. They probably aren’t causing problems until they’re discovered, and it doesn’t take long from discovery for engineers to figure out workarounds.
Both CPUs and browsers make trade-offs between security, complexity, and performance. These trade-offs aren’t simple, because complexity that harmonizes performance with security can cause vulnerabilities.
In both of these cases, some vendors have made the right choices about security even though they may have caused hits to performance or convenience. We would generally prefer products that are safer even when they’re slightly slower, but we never find out which products these are until we’ve made our choices.
Wouldn’t it be great if marketing departments touted security trade-offs as product features?
UPDATE 1/3/18
Intel has issued a statement on the memory protection bug:
Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data.
Recent reports that these exploits are caused by a “bug” or a “flaw” and are unique to Intel products are incorrect. Based on the analysis to date, many types of computing devices — with many different vendors’ processors and operating systems — are susceptible to these exploits.
Intel is committed to product and customer security and is working closely with many other technology companies, including AMD, ARM Holdings and several operating system vendors, to develop an industry-wide approach to resolve this issue promptly and constructively. Intel has begun providing software and firmware updates to mitigate these exploits. Contrary to some reports, any performance impacts are workload-dependent, and, for the average computer user, should not be significant and will be mitigated over time.
Intel is committed to the industry best practice of responsible disclosure of potential security issues, which is why Intel and other vendors had planned to disclose this issue next week when more software and firmware updates will be available. However, Intel is making this statement today because of the current inaccurate media reports.
Check with your operating system vendor or system manufacturer and apply any available updates as soon as they are available. Following good security practices that protect against malware in general will also help protect against possible exploitation until updates can be applied.
Intel believes its products are the most secure in the world and that, with the support of its partners, the current solutions to this issue provide the best possible security for its customers.
So the bug is more widespread but less severe than initially believed. As usual.