The Cyberwar in Ukraine
Who would you bet on to win the game of cyberwar, the best minds in the world or a sad bunch of hacks whose highest professional aspiration is working for a madman?
5G and the Zero Trust Security Model
More than anything, we need network components that are inexpensive and capable of taking part in a comprehensive system of self-checking. We’re more likely to get such a system by building it collaboratively.
Wired Trolls 5G Security
Today’s Internet-based tech press is more concerned with monetizing than websites than with imparting good information. Perhaps this is simply the way media is nowadays, but the tendency to exaggerate seems to be amplified when the press addresses the Internet itself.
DoH Creates More Problems than it Solves
We need to redesign DoH so that it works with DHCP and local policies, not against them. The layered architecture of the Internet and the distributed nature of DNS become nothing more than cruel jokes if this standard is rolled out in its current form.
Shane and Richard on Wi-Fi, Security, and Europe
In this edition of the podcast, Shane and Richard talk about setting up a Wi-Fi network for optimal security and performance, recent developments in security, and what’s going on in Europe with copyright enforcement and privacy.
FBI/DHS Security Report a “Jumbled Mess”
“No one should be making any attribution conclusions purely from the indicators in the [government] report,” tweeted Dmitri Alperovitch, chief technology officer of CrowdStrike, which investigated the DNC hack and attributed it to the Russian government. “It was all a jumbled mess.’’
Making the Internet Secure Again
The Internet utterly depends on the kindness of users. Its free and open nature has always meant that reliable operation is the norm only as long as most users and…
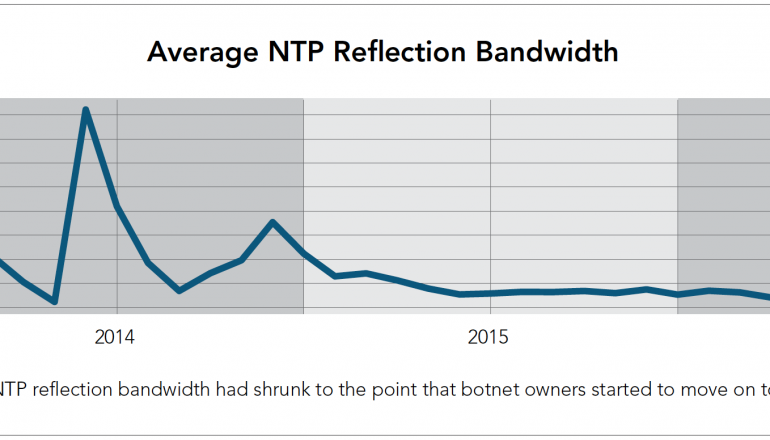
Attacked by Our Toasters
Is there a connection between the FCC’s Open Internet regulations and the recent DDoS attacks on Brian Krebs, OVH, and Dyn DNS? A letter to FCC Chairman Tom Wheeler from…