FBI/DHS Security Report a “Jumbled Mess”
Happy New Year, gentle reader. While we’d all like this year to be better than the last, we’re off to an inauspicious start. The lead story in this week’s tech news is a retraction. A report in last Friday’s Washington Post that said Russian hackers had broken into the nation’s electric grid was wrong. While it accurately reflected guidance sent by FBI/DHS to electric utilities, the guidance was nonsense.
The Burlington Electric Report
The Post story about an alleged Russian hack of Burlington Electric has been rewritten twice. The original story, titled Russian hackers penetrated U.S. electricity grid through a utility in Vermont, U.S. officials say alleged that a laptop connected to the electric grid had been penetrated by Russian malware:
A code associated with the Russian hacking operation dubbed Grizzly Steppe by the Obama administration has been detected within the system of a Vermont utility, according to U.S. officials…
American officials, including one senior administration official, said they are not yet sure what the intentions of the Russians might have been. The penetration may have been designed to disrupt the utility’s operations or as a test by the Russians to see whether they could penetrate a portion of the grid.
Federal officials have shared the malware code used in Grizzly Steppe with utility executives nationwide, a senior administration official said, and Vermont utility officials identified it within their operations.
It turns out the laptop in question wasn’t connected to the grid’s control system at all, so the Post rewrote the story to clarify that point:
A code associated with the Russian hacking operation dubbed Grizzly Steppe by the Obama administration has been detected within the system of a Vermont utility, according to U.S. officials…
Burlington Electric said in a statement that the company detected a malware code used in the Grizzly Steppe operation in a laptop that was not connected to the organization’s grid systems. The firm said it took immediate action to isolate the laptop and alert federal authorities.
On Monday, the Post clarified the story with a new post declaring it a false alarm:
As federal officials investigate suspicious Internet activity found last week on a Vermont utility computer, they are finding evidence that the incident is not linked to any Russian government effort to target or hack the utility, according to experts and officials close to the investigation.
An employee at Burlington Electric Department was checking his Yahoo email account Friday and triggered an alert indicating that his computer had connected to a suspicious IP address associated by authorities with the Russian hacking operation that infiltrated the Democratic Party. Officials told the company that traffic with this particular address is found elsewhere in the country and is not unique to Burlington Electric, suggesting the company wasn’t being targeted by the Russians. Indeed, officials say it is possible that the traffic is benign, since this particular IP address is not always connected to malicious activity.
As crazy as this is, the Post is not to blame.
FBI/DHS Didn’t Correctly Communicate the Event
The sequence of events went like this: Burlington Electric found a virus on an employee’s laptop that looked like Russian hacker code and reported it to the FBI and DHS as they’re supposed to do. The agencies then issued a report to all the other electric utilities warning them to be on their toes for Russian hacker code – known as Grizzly Steppe – found in Burlington. The Post caught wind of the story and rushed it to print.
We can now see that publishing such a preliminary story was ill-advised. In fact, the virus on the laptop is something known as Neutrino, unrelated to Grizzly Steppe.:
U.S. officials are continuing to investigate the laptop. In the course of their investigation, though, they have found on the device a package of software tools commonly used by online criminals to deliver malware. The package, known as Neutrino, does not appear to be connected with Grizzly Steppe, which U.S. officials have identified as the Russian hacking operation. The FBI, which declined to comment, is continuing to investigate how the malware got onto the laptop.
So an employee laptop is found to be infected with a virus and FBI/DHS incorrectly judges it a part of the Russian hacking strategy aimed at DNC email. But it’s just a garden variety virus and the employee is simply reading their Yahoo mail. The news here is FBI/DHS making a bad diagnosis that got leaked to the press long before it should have been reported. And the FBI/DHS diagnosis wasn’t just bad, it was very, very bad.
Grizzly Steppe is an Open Source Hack
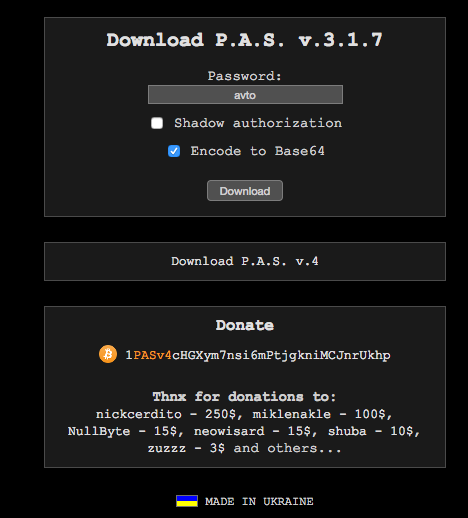
Welcome to Hackerville. Source: WordFence blog
Security firm WordFence has analyzed Grizzly Steppe and found it to be pretty commonplace. It’s an open source hacker’s toolkit called P. A. S. created in Ukraine that anyone could get for free on web. The website has been turned off, but WordFence has screenshots of they way it looked before the hackers went into hiding. The image shows the front end screen.
All you had to do was set up a password, download the code, and get it installed in some computers by sending email with HTML attachments or put it on websites through ads, visible or otherwise. The PAS package uploads attack code to the web and then downloads it to victim computers.
Once installed, the criminal in control of the end user computer gets to see what you’re doing and potentially control your computer. There are lots of ways to go that, and this is an especially easy one. It should be easy for FBI/DHS to recognize it where it really exists – WordFence decrypted the attack code – but somehow they managed to botch it.
WaPo consulted with security professionals who panned the government report as too vague and wishy-washy:
The discovery of the laptop issue has prompted criticism that the government provided overly broad information to companies that was not effective in isolating Russian government hacking.
“That report offered no technical value for defenders,” Lee said. “It was very much high level and nothing in there was specifically descriptive of Russian activity.”
Some in the administration are concerned that this episode with the Vermont utility will cause industry officials to avoid sharing information with the government, for fear that it will be leaked. The company in this case, the U.S. official said, “did what it was supposed to do.”
FBI/DHS Need to Up Their Game
Essentially, FBI/DHS described the generic attack and provided utilities with a list of perfectly safe IP addresses. As one expert put it:
“No one should be making any attribution conclusions purely from the indicators in the [government] report,” tweeted Dmitri Alperovitch, chief technology officer of CrowdStrike, which investigated the DNC hack and attributed it to the Russian government. “It was all a jumbled mess.’’
While some are proclaiming this debacle is an example of the fake news problem hitting the mainstream media, it’s more accurate to see it has an example of the government failing to provide sound, expert judgment on a technical matter that sits on the very edge of the technical expertise in the nation’s smaller electric utilities. The story the Post wrote was consistent with what the government was telling the utilities and therefore not fake.
The story also raises questions about leakers. My next post will elaborate on that problem. But for now, public utilities need to take a “trust but verify” approach to guidance from FBI/DHS on hacks. The agencies have people on the payroll who understand these issues, but they’re not writing the advice the agencies send out. It appears that Dilbert’s boss has taken that job for himself.



