Protecting Mossack Fonseca’s Panama Papers
The Panama Papers – the 2.6 TB trove of legal files from Panamanian law firm Mossack Fonseca detailing dodgy tax avoidance schemes – is a great lesson in security. While it’s not completely certain how the firm was hacked, the best available evidence suggests it didn’t pay nearly enough attention to basic security practices.
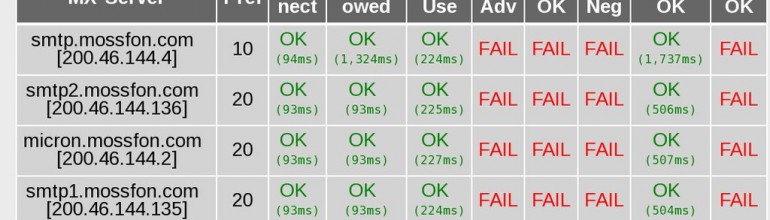
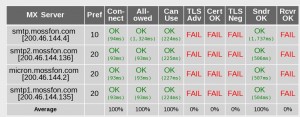
The firm deals with other law firms and with banks with clients concerned about privacy and tax avoidance. While it promised top-notch security, it failed to keep its content management system up to date despite numerous well-known vulnerabilities. According to Chris Soghoian, the firm also failed to enable basic email security.
Buggy Software
The firm uses WordPress and Drupal, open source blogging and content management systems (CMS) that are known for endless vulnerabilities that require endless updates. As Thomas Fox-Brewster explains in Forbes:
Forbes discovered the firm ran a three-month old version of WordPress for its main site, known to contain some vulnerabilities, but more worrisome was that, according to Internet records, its portal used by customers to access sensitive data was most likely run on a three-year-old version of Drupal, 7.23. That platform has at least 25 known vulnerabilities at the time of writing, two of which could have been used by a hacker to upload their own code to the server and start hoovering up data.
To make matters worse, The firm kept its files neatly organized in a folder per client, so it was pretty easy for the journalists investigating the story to connect the dots.
It’s not that surprising that Mossack Fonseca doesn’t have much of a handle on IT security as its basic business was simply creating shell companies and occasionally finding fake directors to stand in for real owners. This is not a high tech pursuit, and a lot of its customers were pretty small. The firm apparently would setup an offshore shell for as little as $1000, which doesn’t leave much room for highly skilled programmers. But it doesn’t take much skill to update a WordPress blog or an open source CMS.
Impressive Software
What is impressive is the fact that a consortium of 400 journalists was able to take a year mining 2.6 TB worth of legal records without anyone outside the group knowing about it. The consortium – known as the International Consortium of Investigative Journalists (ICIJ) – used a suite of customized, open source security and document analysis software to mine the trove for connections while keeping it safe from prying eyes. The chief security elements are a disk encryption tool known as VeraCrypt and secure messaging tools such as Jabber, Signal, Telegram or Wickr.
According to Forbes, the journalists created their own little version of Facebook:
A separate site, a “virtual newsroom” as Cabra called it, did include an extra protection: two-factor authentication using Google Authenticator, providing an additional one-time code to enter after the password was provided. In that space, reporters could update colleagues with their latest story ideas, all delivered via a Facebook-like newsfeed, whilst using the chat feature for further collaboration. Again, the social network was constructed on open source software, Oxwall. (ICIJ makes some of its own tools open source too, the most recent addition on Github being a command line tool for content analysis).
Completely apart from the virtual newsroom, each journalist had a battery of analysis tools available:
The search tool, allowing reporters to hunt for names like Putin or places like the British Virgin Isles, was based on Apache Solr, used by a large number of search-heavy organizations, including DuckDuckGo, a privacy-focused tool. Solr was combined with Apache’s Tika, an indexing software that can parse different file types, be they PDFs or emails as in the Panama Papers, drawing out the text from the non-essential data. Layered on top was the shiny interface, built using Blacklight, another open source development.
I suppose the nature of story drove home the importance of paying attention to security, encrypting everything, and using secure modes of communication. The last thing the reporters wanted, after all, was for Mossack Fonseca or its shady clients to get wind of what they were doing and spin the story their own way. Not that they didn’t try.
Mossack Fonseca’s Story
When the firm caught wind of an early breach, it did notify clients and take some measures to protect their information, but not nearly enough. Like a lot of firms whose systems are breached, they may have thought one or two little patches solved the problem. But the hacker had probably installed some software inside their network that went undetected. It takes a long time to export that much information so the hack itself ran even longer than the year of investigation by the press.
The lesson is that maintaining privacy takes a lot of work, but most of it is less a matter of hiring geniuses than of being constantly vigilant, keeping software up to date, and using an array of tools to do a number of small but important things.
You would certainly think that an evil genius law firm dealing with the criminal underworld would take better care of their business than this, which tends to support the firm’s claims that most of its business was lawful. This could just be a case of a few bad actors doing dodgy deals, but it could also be a case of underworld having a hard time getting good help.
Where do the Bond villains recruit anyway?