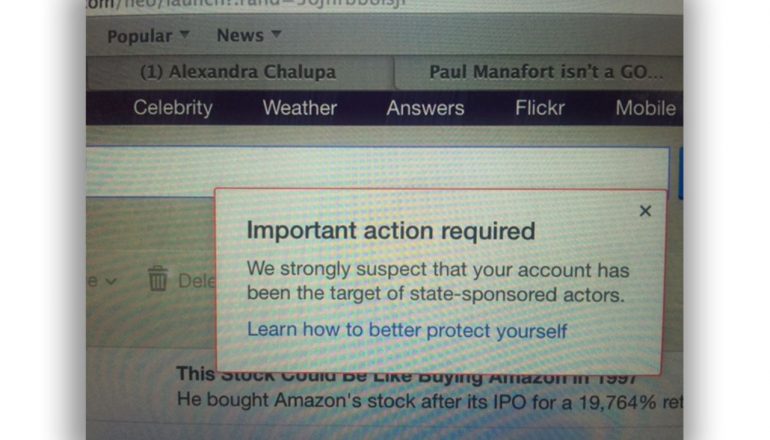
Russia’s Unconventional Election IT Strategy
It turns out my post on the digital campaign tools of the two major presidential candidates was a bit incomplete because it didn’t address outsourcing to foreign powers. The tech…
Apple, FBI Talks Need Engineers
Electrical Engineering Times makes a sage, if somewhat obvious observation about the FBI/Apple dispute about unlocking the iPhone 5s used by dead terrorist Syed Farook: The dispute between Apple and…
Bennett on cybersecurity: ‘We want networks to compensate for errors in judgment’
[powerpress] In the latest High Tech Forum podcast, Richard Bennett sat down with Shane Tews, chief policy officer at 463 Communications, a firm that advises high-tech organizations on Internet policy….
DARPA Enlists Hackers
It’s no secret that government initiatives around cybersecurity haven’t lived up to expectations. While they succeed in creating controversy – such as the recent hubbub over the so-called “Internet Kill…
Saving the Internet from its Friends
I’m going to Australia in April to give a keynote on the innovation potential of Next Generation Networks for the Australian Telecom Users Group. As you probably know, Australia has…